If the journey outlined above sounds achievable yet daunting, you’re not alone. HireRoad was built to collapse the distance between intent and execution. Our unified analytics and compliance platform centralizes employee records, automates control evidence, and surfaces real-time risk dashboards tailored for HR leaders. Think of it as your co-pilot for every step—from scoping and gap assessments to perpetual monitoring—so you can focus on the strategic narratives that set your organization apart. Book a free demo with PeopleInsight by HireRoad today and discover how seamless, data-driven SOC 2 Compliance can be.
- Product
-
-
PeopleInsight by HireRoad
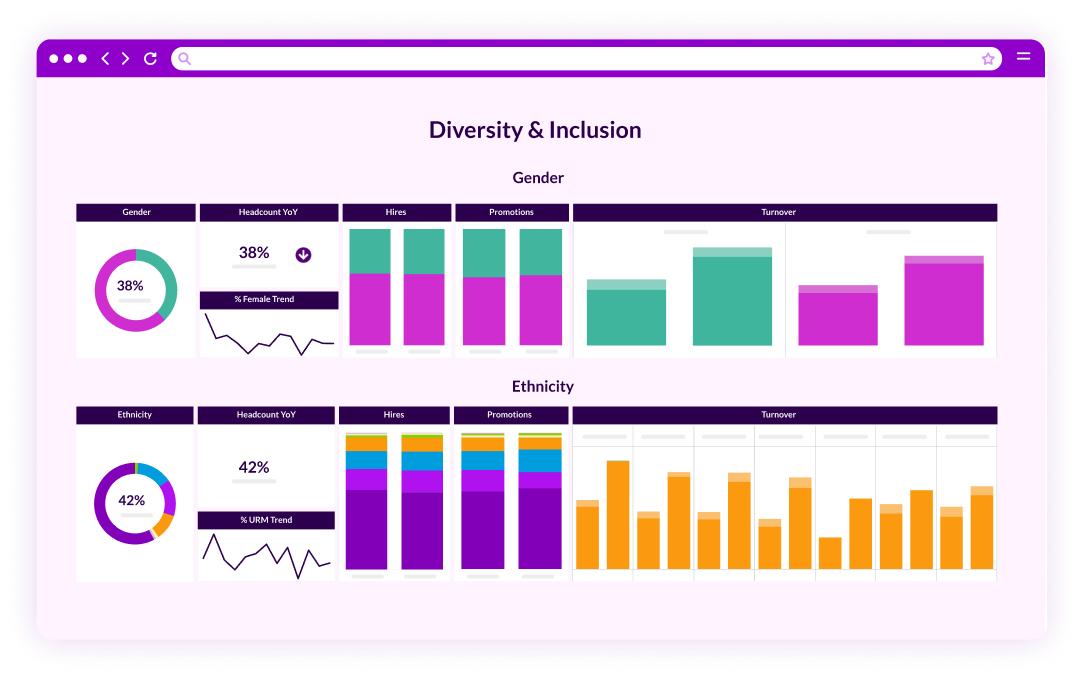
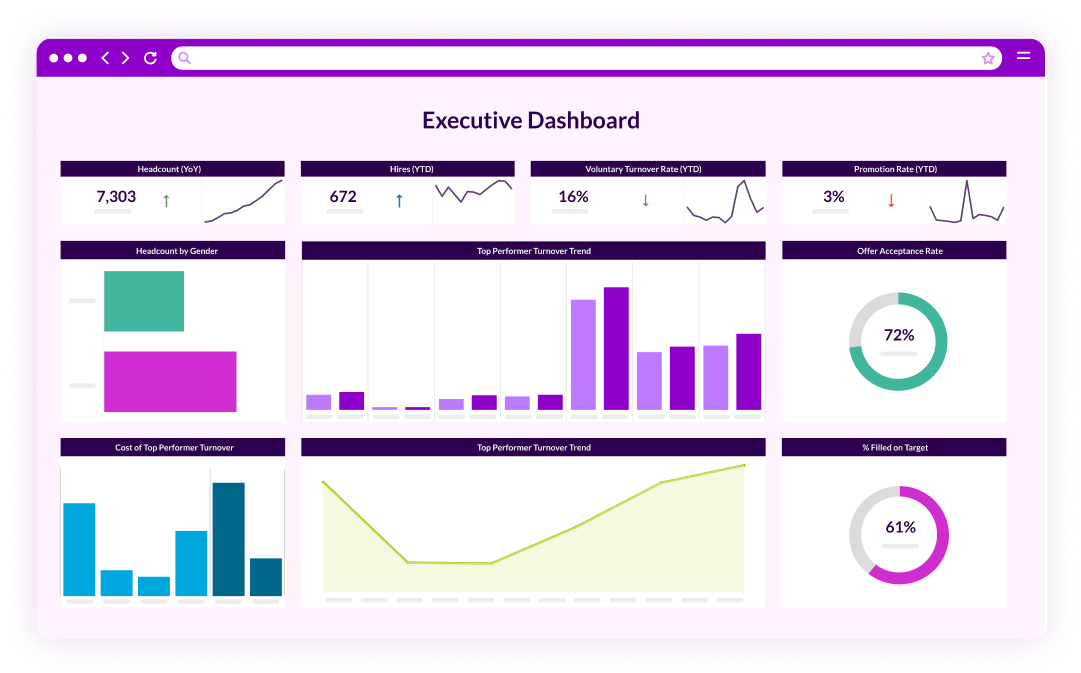
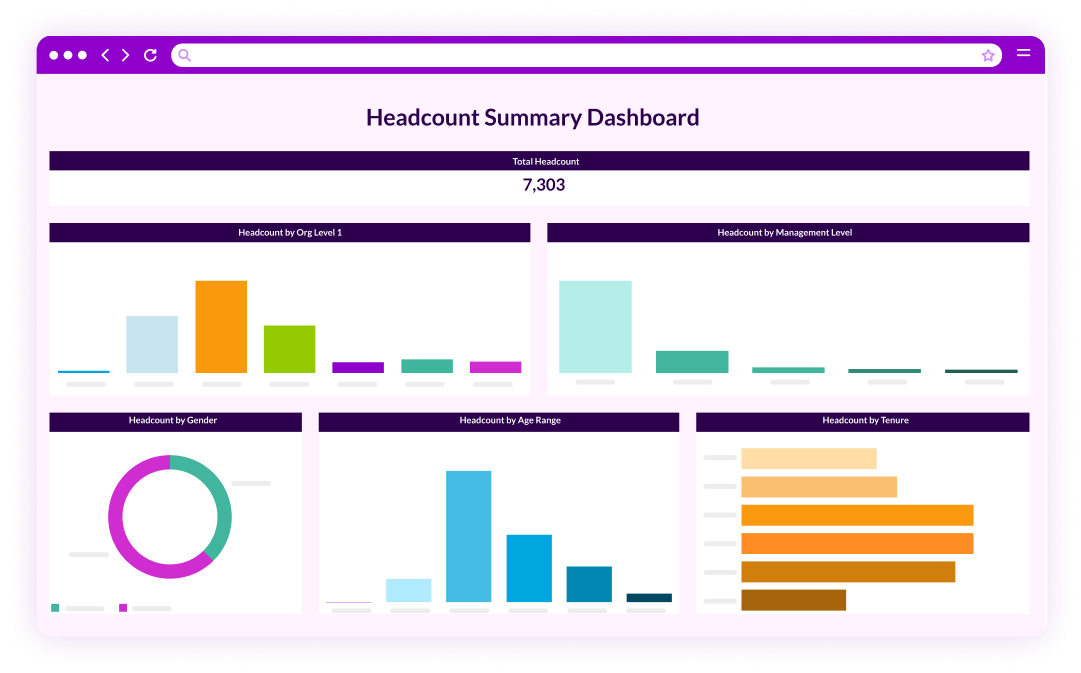
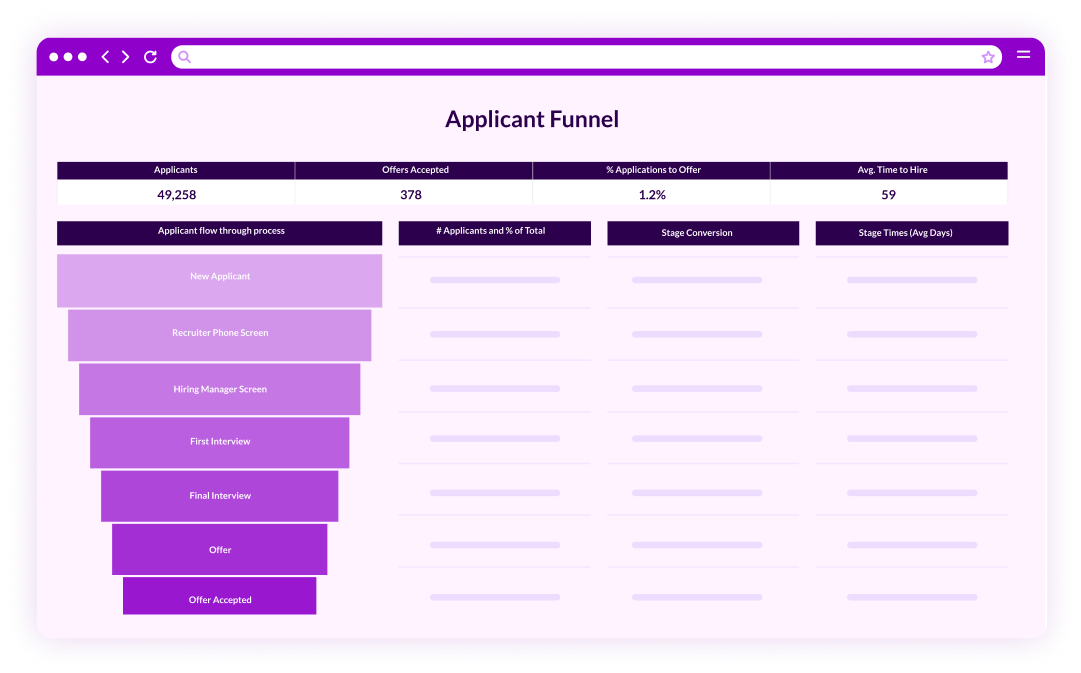
We transform your HR and TA data into intuitive dashboards in just 5 days – no data expertise required.
-
-
-
-
- Why PeopleInsight
-
- Use Cases
-
-
HCM/HRIS
-
-
-
- Resources
-
- About
-
- Request a Demo